Sensitive Data
How to set up the Sensitive Data integration
If your app is collecting PII or other sensitive information, you will likely want enhanced data security features. The Sensitive Data integration gives you the tools you need to protect your users' data.
With this integration you can:
- Automatically encrypt and decrypt sensitive user data.
- Use new Python encrypt and decrypt APIs.
- Limit access to sensitive data in Console to privileged team members.
- Automatically encrypt all media (e.g. images, files).
- Automatically encrypt
httpandwsdata (e.g. to protect auth tokens). - Expire sensitive data after 24 hours.
For a more detailed look of how the Sensitive Data integration works, check out this guide:
Add the integration
In your app’s integration folder, create a new file called sensitive_data.yaml and copy this code into it:
type: meya.sensitive_data.integrationAdvanced settings
The Sensitive Data integration has optional properties you can set to get even more control over what data is considered sensitive.
type: meya.sensitive_data.integration
enabled: true # Optional. Default: true
transport: true # Optional. Default: true
transcript: true # Optional. Default: true
If the integration file does not exist, sensitive data is disabled. The presence of this file impliesenabled: true.
transportrefers to Websocket and HTTP data.
transcriptrefers to events, data scopes, and media.Learn more: What gets encrypted?
Example
Let’s add a flow that we can use to test the sensitive data features.
Add a test flow
In your app’s flow folder, create a file called hi.yaml and copy this code into it:
triggers:
- keyword: hi
steps:
- say: Hi!
- ask_form: What is your email address?
expect: email_address
sensitive: trueSave the new files and push them to the Grid by running these commands in your terminal:
meya format
meya pushTest it out
Let’s test the app to see what conditions result in data being encrypted.
- Open your app’s Simulator and trigger the
hiflow. Check the logs for ameya.form.event.submitentry and confirm that the email you entered is unencrypted.
Since thethread.modeisbot, thesubmitevent is not encrypted, even though the input form was marked as sensitive.Learn more: Non-bot mode encryption
Take a look at one of the meya.http.entry.response entries belonging to the same trace_id. You should see one or more encrypted fields:
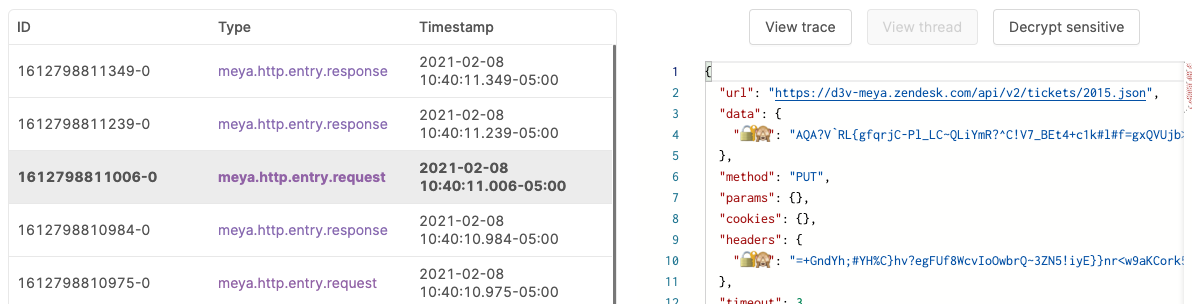
Test agent mode
Let’s test as if the user is talking to an agent. We’re expecting all communication between the user and agent to be encrypted now that we’ve enabled the Sensitive Data integration. Let’s try it out.
- Update
hi.yamlto temporarily switchthread.modeto agent:
triggers:
- keyword: hi
steps:
- say: Hi!
- thread_set:
mode: agent
- ask_form: What is your email address?
expect: email_address
sensitive: true
- thread_set:
mode: bot
If you have a customer support integration set up, you can transfer the conversation to the agent instead of updatinghi.yaml.
Save the file and push it to the Grid:
meya format
meya pushTrigger the hi flow again and check the submit event in the logs:
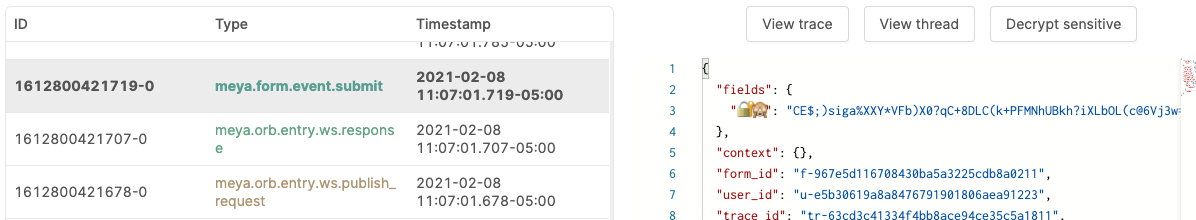
If your Meya user account has permission to decrypt the entry, click the Decrypt sensitive button to view the unencrypted data.
Great! You’ve set up the Sensitive Data integration.Sensitive data: scopes, Jinja2 filters, and Python APIs
Sensitive data overview
Updated 9 months ago
